A comprehensive security platform for penetration testing, vulnerability assessment, and advanced security operations with unparalleled speed and precision.
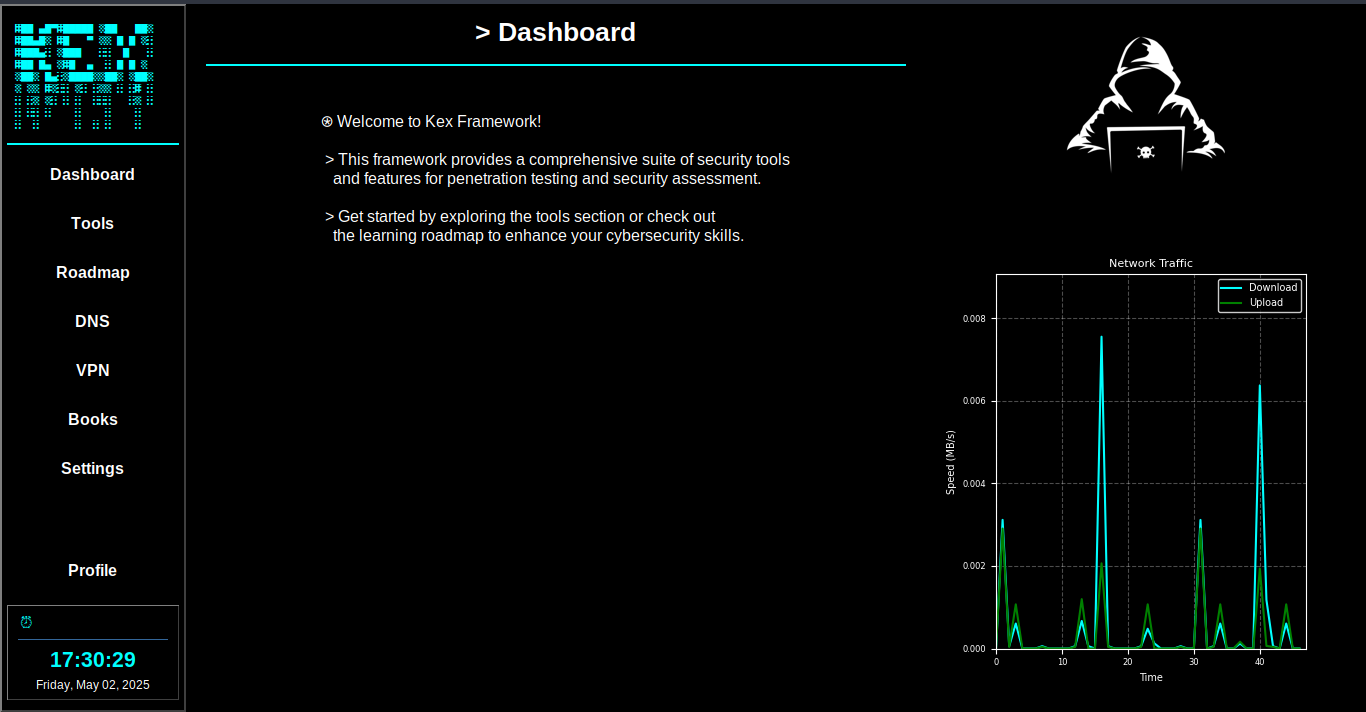
A comprehensive security platform for penetration testing, vulnerability assessment, and advanced security operations with unparalleled speed and precision.

A next-generation security platform built for modern threats with advanced tools and intuitive workflows.
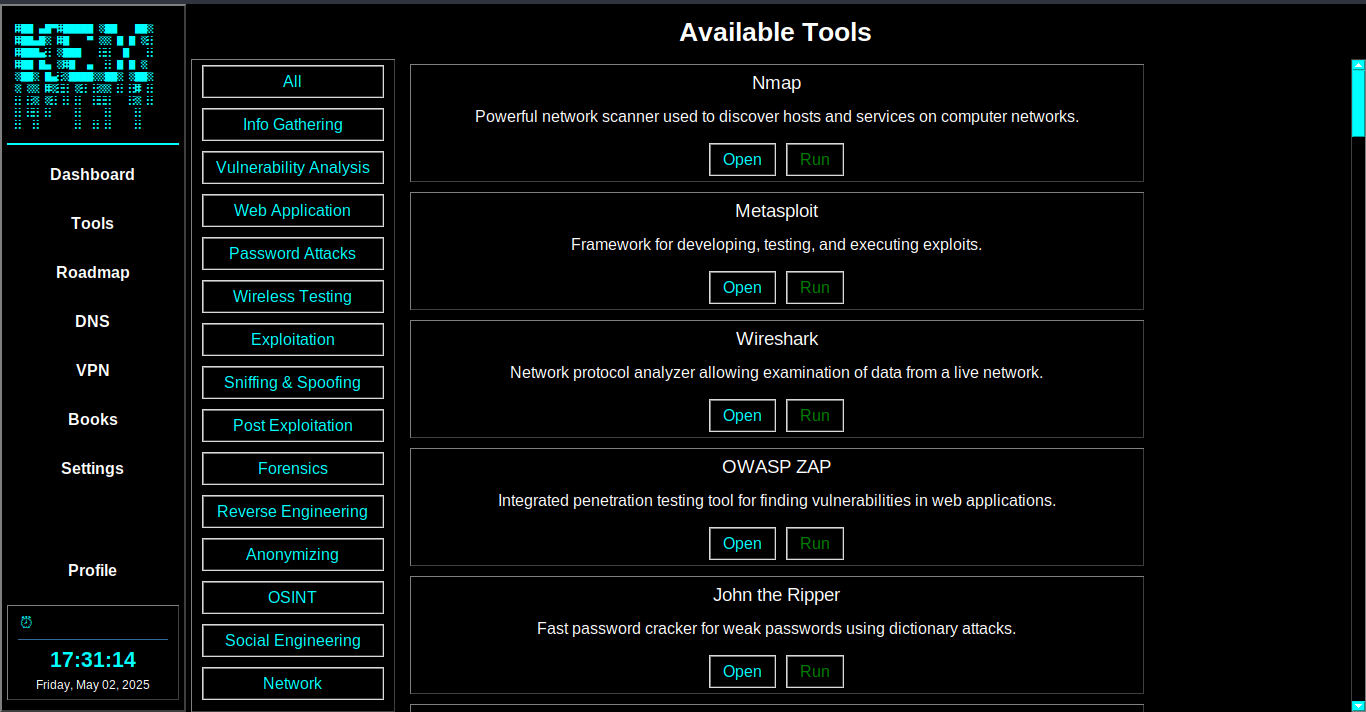
Comprehensive suite of security tools in a single unified interface for streamlined operations.
Advanced tools for security assessment, vulnerability scanning, and penetration testing.
Real-time monitoring of network traffic with detailed visualization and analysis.
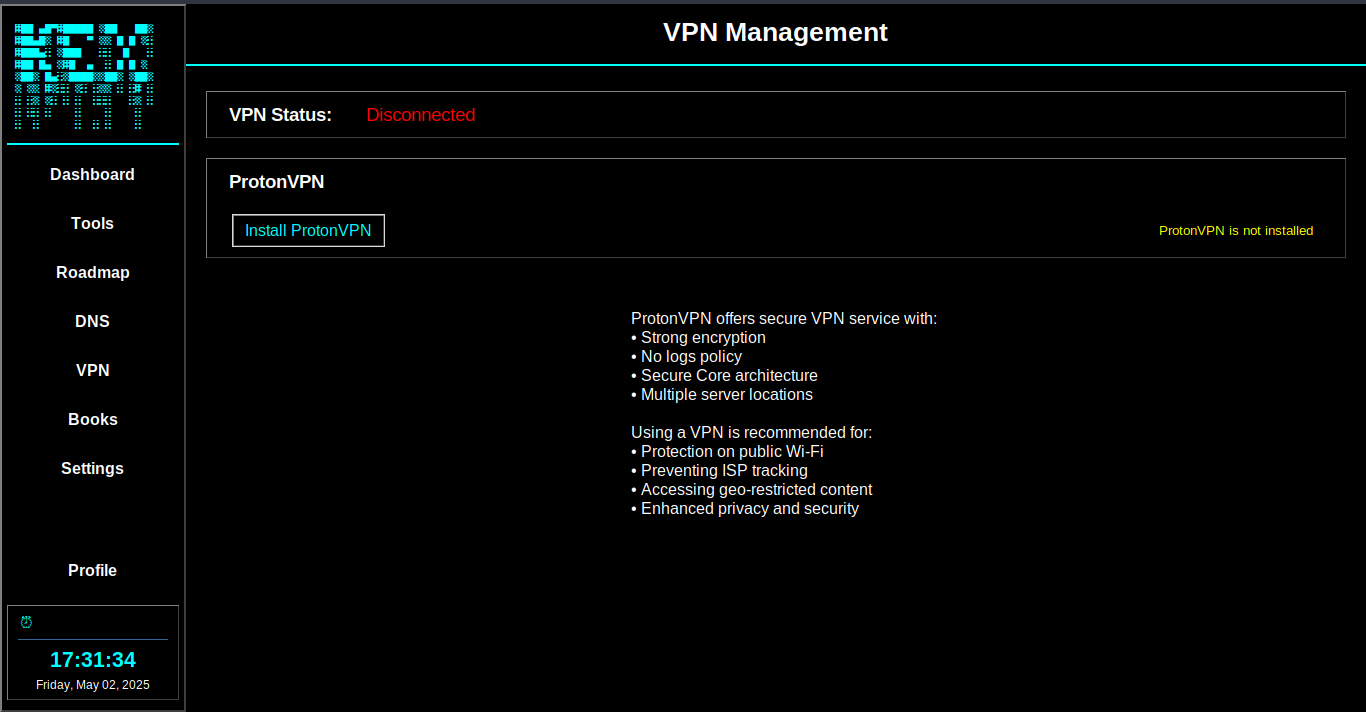
Built-in ProtonVPN support for anonymous and secure connections during security operations.
Easily extend functionality with custom modules and plugins for specialized security tasks.
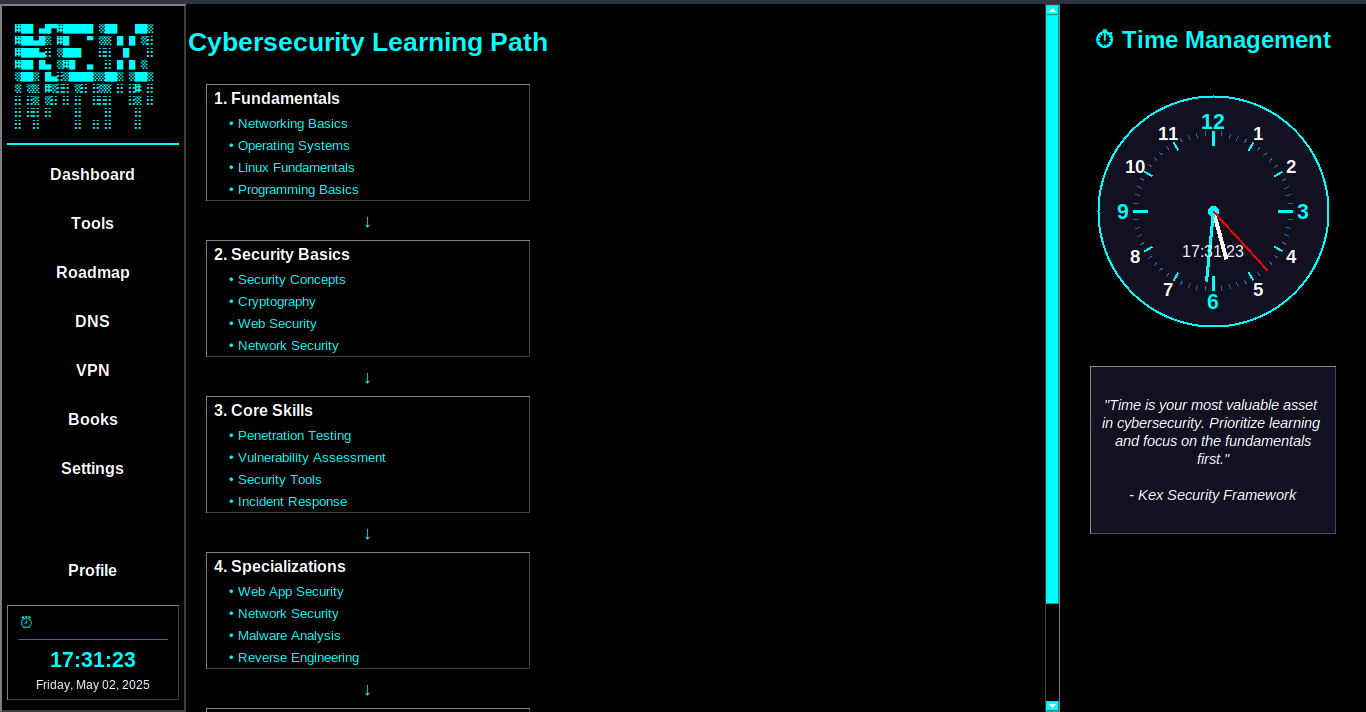
Integrated cybersecurity learning roadmap and resources for skill development.
Get Kex Framework up and running in seconds with simple installation commands.
# Install python dependencies (Linux):
pip3 install -r requirements.txt --break-system-packages
# For AppImage installation (Linux):
chmod +x Kex-x86_64.AppImage
./Kex-x86_64.AppImageAvailable as both a Python application and Linux AppImage for easy distribution and deployment across security environments.
Get Kex running on your system with one of our pre-built packages.
Portable, self-contained executable. No installation required.
This AppImage is exclusively available through our official Telegram channel.
A comprehensive suite of specialized tools designed for modern security professionals.
Open-source intelligence gathering and reconnaissance tools for comprehensive target analysis.
Sophisticated decompilers and analysis tools for understanding application internals and code behavior.
Intelligent scanning engines for vulnerability detection with customizable assessment templates.
Advanced network analysis and penetration testing utilities for security infrastructure validation.
Authentication systems testing and security access control validation frameworks.
Security defense assessment and hardening recommendations based on threat intelligence.
See how security professionals use Kex to secure systems and protect organizations.
Comprehensive OSINT gathering and target reconnaissance for pre-engagement planning.
View Case StudyDetailed network vulnerability assessment and visualization for threat detection and mitigation.
View Case StudySystem hardening and defense analysis with comprehensive security reporting and analytics.
View Case StudyExplore the visual elements of the Kex security framework and its applications.

Connect with security professionals, contribute to the project, and stay updated.